Anti-censorship team updates from September and October, 2021
This is an overview of the activities that the anti-censorship at Tor has been up to for the last two months! We work with many other teams at Tor to ensure that users all over the world can circumvent censorship safely.
Snowflake pluggable transport
Snowflake is a WebRTC-based pluggable transport (PT) that ships in stable versions of Tor Browser. Snowflake is still under active development as we add new features, fix bugs, and aim to improve the performance and censorship resistance of this PT.
We’ve also made it easier for people to run Snowflake proxies. Thanks to idk from I2P, our Snowflake proxy code can now be imported as a Go library. Meskio has also created a new Debian package for the Snowflake client and proxy to ease the installation process. This package is waiting for review.
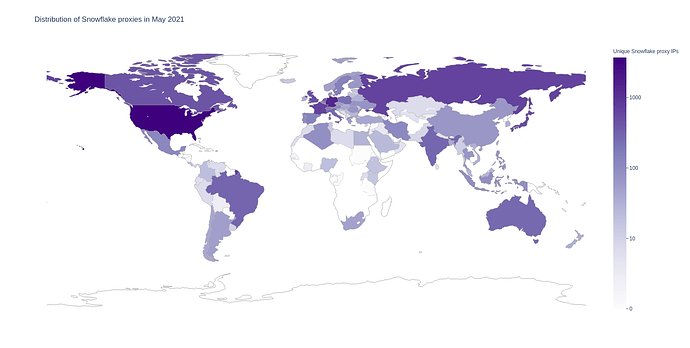
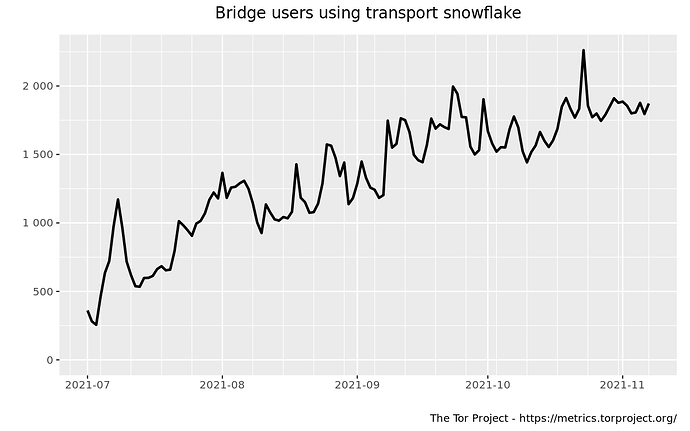
The usage metrics of Snowflake and our pool of volunteer proxies has continued to grow. We now boast over 12,000 unique Snowflake proxy IPs daily, supporting over 2,000 Snowflake clients. Going forward, one of our focuses will be to ensure that the performance and user capacity of Snowflake will continue to scale.
As a first step in our efforts to understand and improve the performance of Snowflake, we have been working with the Shadow team to ensure support for Go networking libraries in the Shadow network simulator. This will allow us to test out performance enhancing features on a test network before deploying them to the real world.
Finally, we worked on some minor changes and bug fixes:
-
We included a bug fix for Snowflake proxies in snowflake#40055 and updates to our documentation and READMEs.
-
We factored out Snowflake’s geoip code into a separate library that can be used by multiple programs in team#32
Resource distribution
rdsys is our new multi-purpose resource distribution system. The motivation of building it was to provide a modular alternative to BridgeDB, allowing us to easily plug-in new distribution channels, apply these channels to any resources that need to be fetched by users facing censorship.
Meskio has been leading the effort to use rdsys as the backend for BridgeDB and has made a lot of progress in the last few months:
- Added support for parsing bridge-descriptors and networkstatus files using the zoossh library (rdsys#62).
- Honour the operator’s choice of distribution method (rdsys#39).
Meskio has also been working with the applications team on streamlining the bridge/anti-censorship settings in Tor Browser. As a part of this work, he implemented the ability to distribute circumvention settings as part of the moat API (rdsys#59).
We’ve begun migrating GetTor backend functionality to rdsys as well. GetTor is a tool to allow users facing censorship to download Tor Browser in places where the usual torproject.org download page is blocked. The integration with rdsys will allow us greater flexibility in GetTor distribution channels and make it easier to maintain. This is still a work in progress and related issues can be tracked on our rdsys issue tracker.
Eventually, we will have an automated process to distribute the most up-to-date bundles when a new version of Tor Browser is released. Until then, we’ve been updating our releases manually (gettor#82).
We maintain a tool called bridgestrap to test the reachability of Tor bridges. This is useful as a debugging tool for relay operators and for annotating whether bridges are running properly in our bridge distribution system. These last few months we’ve made progress on stabilizing the accuracy and performance of bridgestrap with the help of Alex and Roger merging fixes in core Tor:
- Fixed an issue with false errors in bridgestrap (bridgestrap#7)
- Helped debug a tor bug that occurs when a known bad bridge is included in the torrc file (tor#40396)
Censorship Rapid Response
We recently received some new funding to work on rapidly responding to censorship! This work will cover censorship measurement and analysis efforts to detect and understand how Tor is censored, which will guide our implementation of new efforts to keep Tor accessible to all users.
Our recent work on this includes:
- Ongoing discussion and collaboration with the Community team to understand the censorship of Tor in Turkmenistan (community#40030).
- Cecylia has been working on censorship monitoring infrastructure to facilitate bridges with rotating IP addresses.
Thanks for Reading!
Please feel free to reach out with questions or comments ![]() . If you’d like to join our weekly meetings, we meet every Thursday at 16 UTC on the OFTC IRC network in #tor-meeting. More information on our team is available on our team wiki page.
. If you’d like to join our weekly meetings, we meet every Thursday at 16 UTC on the OFTC IRC network in #tor-meeting. More information on our team is available on our team wiki page.