Hi,
New update: In the last few weeks, internal political conflicts and
other events[1] in Turkmenistan have led to another wave of censorship
on Tor and anti-censorship tools. Tor bridges have been one of the few
free alternatives for people in Turkmenistan to connect with the world
and access the open Internet.
If you have access to an IP range that has never seen the light of day,
a stable residential connection, or access to your university network,
you can help thousands of people connect to the internet in
Turkmenistan.
Tor bridges running on residential connections, on dynamic IPv4 address,
or on unblocked IP ranges are effective, but are regularly discovered
and blocked by censors, thus making us to call for new bridges. These
bridges must run on specific obfs4 ports: 80, 8080, or 443. See below
the example of torrc for your bridge. If it's your first time running a
bridge, please follow our official guide:
<https://community.torproject.org/relay/setup/bridge/>\.
Finding an IP range that is unblocked-in the country is not easy.
However, bridges in universities and IP ranges in US have been of great
help to people in Turkmenistan.
Please note that it's not possible to run IPv6-only bridges and
Turkmenistan has a very small adoption of IPv6.
If you run a bridge to help people in Turkmenistan, send your bridge
line to frontdesk@torproject.org. We will share your bridge with people
that really need it!
A bridge line is composed of:
IP:OBFS4_PORT FINGERPRINT cert=obfs4-certificate iat-mode=0
If you need help to build your bridge line, please check the official
guide: Tor Project | Post-install
## Other Pluggable Transports
- Snowflake has been blocked in the country since 2021:
- STUN servers are running on blocked IP ranges
- When we found an available STUN server, it didn't find a proxy to
match (probably because of the TM's IP range rules). For more
information, see this ticket[2].
- Meek[3] (domain fronting) is one of the few techniques that
consistently works, but with reduced speed. While there is a dedicated
bridge for TM, its cost is high.
- Conjure[4] was successfully tested, but more development hours are
still needed for its maintenance and stabilization. Currently it is
only available on Tor Browser Alpha and some other Tor powered apps.
- WebTunnel[5] could potentially work, but like obfs4 bridges, it
depends on whether the website is hosted on an IP range that is not
blocked in Turkmenistan.
## Research and other resources
If you would like to learn more about censorship in Turkmenistan,
ntc.party is a great resource (posts in Russian):
Turkmenistan - NTC
And this paper (2023) about measuring Internet censorship in TM:
"Measuring and Evading Turkmenistan's Internet Censorship: A Case Study
in Large-Scale Measurements of a Low-Penetration Country" (Sadia Nourin,
Van Tran, Xi Jiang, Kevin Bock, Nick Feamster, Nguyen Phong Hoang, Dave
Levin) 2023-04-17
[2304.04835] Measuring and Evading Turkmenistan's Internet Censorship: A Case Study in Large-Scale Measurements of a Low-Penetration Country
https://tmc.np-tokumei.net/
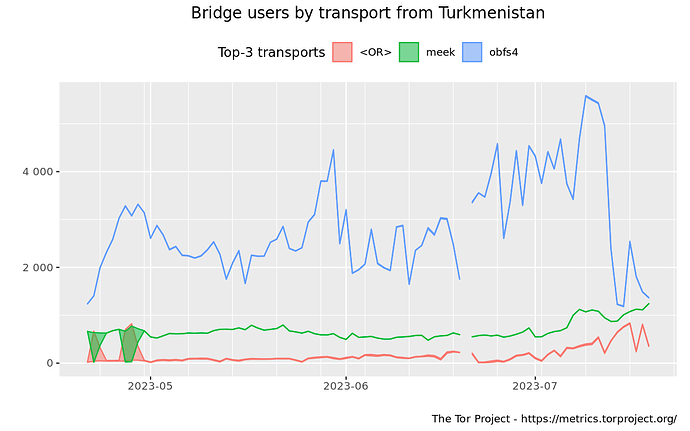
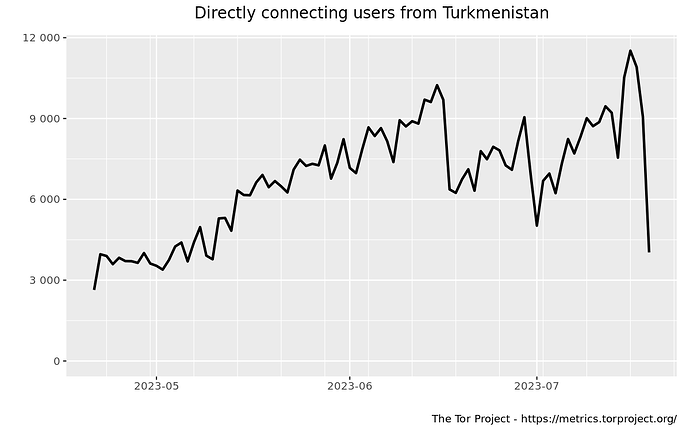
## Tor metrics
You can follow a rough estimate of Tor usage in Turkmenistan here:
- Users – Tor Metrics
- Users – Tor Metrics
## torrc example
BridgeRelay 1
ORPort 127.0.0.1:auto
AssumeReachable 1
ServerTransportPlugin obfs4 exec /usr/bin/obfs4proxy
ServerTransportListenAddr obfs4 0.0.0.0:8080
ExtORPort auto
Nickname helptm
ContactInfo <please-add-your-email-here>
Log notice file /var/log/tor/notices.log
# If you set BridgeDistribution none, please remember to email
# your bridge line to us: frontdesk@torproject.org
BridgeDistribution none
Thank you,
Gus
Notes
[1]
Turkmenistan's Authoritarian President Sacks Several Top Officials
Turkmenistan opens futuristic city dedicated to leader | Reuters
[2]
Blocking of Snowflake in Turkmenistan, 2021-10-24 (#40024) · Issues · The Tor Project / Anti-censorship / censorship-analysis · GitLab
[3]
Relay Search
[4]
🔍 Call for Testers: Help the Tor Project to test Conjure on Tor Browser Alpha!
[5]
[tor-relays] (Announcement) WebTunnel, a new pluggable transport for bridges, now available for deployment
On Tue, Apr 04, 2023 at 12:46:47AM -0300, gus wrote:
Hello,
Another update:
As it's very hard to get a vantage point in the country[1], we've asked
feedback from users to understand what works there. But, if by any chance
you have access to a machine hosted there, do let me know! You can
contact me in private. 
Based on user feedback, we learned that obfs4 bridges running on
residential connections + port 80, 443 or 8080 works in Turkmenistan.
Last week I asked some operators to change their bridge obfs4 port and
it worked!
Unfortunately, users reported that censors blocked some bridges. You can
even see that on Tor Metrics graph. For example:
- Relay Search
- Relay Search
If you're operating these bridges and can easily rotate the IP address, please
do!
Finally, if you want to learn more about censorship in Turkmenistan, you
can check this great presentation[2] from last year.
Thanks for running bridges!
Gus
[1] VPS в Туркменистане - #9 by s11 - Turkmenistan - NTC
[2] Censorship in Turkmenistan Slides.pdf - Google Drive
On Thu, Mar 23, 2023 at 01:00:17PM -0300, gus wrote:
Hello, just a quick update:
Some friends from Turkmenistan told me that they don't think this new
round of online censorship is related to the upcoming elections,
because it's just a "formal" event. In general, they said, shutdowns and
internet disruptions are motivated by other events like:
- when Russian Duma speaker arrived in TM
- the wedding day of the president's grandson
Anyway, today we tested some of bridges that you shared with us and I replied
back saying which ones worked and which ones didn't.
Thank you for running a bridge!,
Gus
On Wed, Mar 22, 2023 at 04:25:05PM -0300, gus wrote:
Dear Relay operators community,
The parliamentary elections in Turkmenistan are coming up very soon on
March 26th[1], and the Turkmen government has tightened internet censorship
and restrictions even more. In the last few months, the Anti-censorship
community has learned that different pluggable transports, like
Snowflake, and entire IP ranges, have been blocked in the country.
Therefore, running a bridge on popular hosting providers like Hetzner,
Digital Ocean, Linode, and AWS won't help as these providers' IP ranges
are completely blocked in Turkmenistan.
Recently, we learned from the Anti-censorship community[2] and via Tor user
support channels that Tor bridges running on residential connections
were working fine. Although they were blocked after some days or a week,
these bridges received a lot of users and were very important to keep
Turkmens connected.
How to help Turkmens to access the Internet
You can help Turkmens to access the free and open internet by running an
obfs4 Tor bridge! But here's the trick: you need to run it on a
residential connection -- you won't need a static IPv4 --, and it would
ideally be run on more robust hardware than just a Raspberry Pi
(although that can help, we have found they can get overloaded).
You can set up an obfs4 bridge by following our official guide:
Tor Project | Bridge
After you setup a new bridge, you can share your bridge line with the
Tor support team at frontdesk@torproject.org, and we will share it with
users.
A complete bridge line is composed of:
IP:OBFS4_PORT FINGERPRINT cert=obfs4-certificate iat-mode=0
Check this documentation to learn how to share your bridge line:
Tor Project | Post-install
Just sharing your bridge fingerprint is not the best, but it's fine.
You can read more about censorship against Tor in Turkmenistan here:
- [Turkmenistan] Number of directly connecting users is going down (#40029) · Issues · The Tor Project / Anti-censorship / censorship-analysis · GitLab
- Snowflake blocked:
Blocking of Snowflake in Turkmenistan, 2021-10-24 (#40024) · Issues · The Tor Project / Anti-censorship / censorship-analysis · GitLab
Thank you for your support in helping to keep the internet free and open
for everyone.
Gus
[1] 2023 Turkmen parliamentary election - Wikipedia
[2] Turkmenistan - NTC
Bidirectional DNS, HTTPS, HTTP injection in Turkmenistan · Issue #80 · net4people/bbs · GitHub
--
The Tor Project
Community Team Lead
_______________________________________________
tor-relays mailing list
tor-relays@lists.torproject.org
tor-relays Info Page
--
The Tor Project
Community Team Lead
--
The Tor Project
Community Team Lead
_______________________________________________
tor-relays mailing list
tor-relays@lists.torproject.org
tor-relays Info Page